Originally published September 23, 2018 @ 2:01 pm
With the growing number of network-enabled devices in your home, meaningful security becomes elusive. The first step to addressing the situation is knowing what you have. A few examples below use the nmap utility to scan your local network and detect active devices and services.
Install nmap-to-CSV conversion utility
cd ~ && git clone https://github.com/maaaaz/nmaptocsv /bin/cp -p ./nmaptocsv/nmaptocsv.py /usr/bin/ chmod 755 /usr/bin/nmaptocsv.py
In my experience, the nmaptocsv.py worked only with Python 2.7, so you may need to install this version as an alternative and update the script to use it.
sed 's/env python$/env python2.7/g' -i /usr/bin/nmaptocsv.py
Define scan parameters
# Current date and time
d=$(date +'%Y-%m-%d_%H%M%S')
# Output file
f="/var/log/nmap_${netwk}_${netwk_mask}_${d}.txt"
# Network to scan
netwk=192.168.122.0
# Network mask
netwk_mask=24
# Timeout to use with nmap
tout=600
# Set number of parallel scans to 10 times the number of CPU cores
(( p = `grep -c proc /proc/cpuinfo` * 10 ))
Run the scan
nmap -sn ${netwk}/${netwk_mask} -oG - 2>/dev/null | \
awk '$4=="Status:" && $5=="Up" {print $2}' | sort -uV | \
xargs -n1 -P${p} -I% sh -c \
"nmap --host-timeout ${tout} -p 1-65535 -O -sV -sS -T4 % -oG - 2>/dev/null | \
nmaptocsv.py -d';' -f ip-fqdn-port-protocol-service-version-os | \
tee -a "${f}""
Cleanup the output file
sed '2,${/FQDN/d;}' -i "${f}"
sed '/^\s*$/d' -i "${f}"
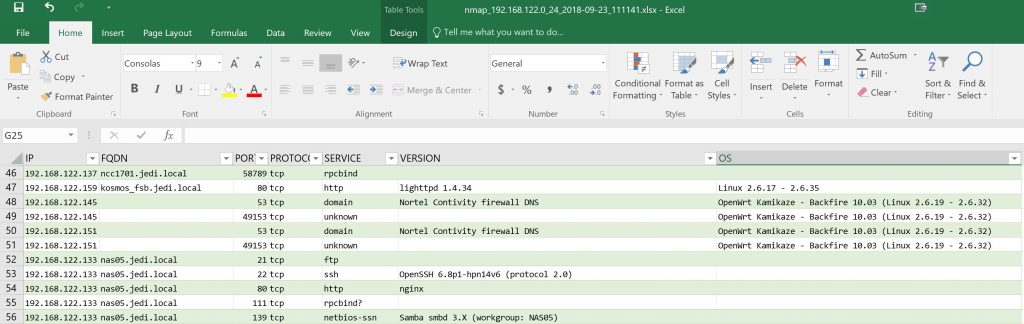
Converted to spreadsheet the end result may look something like this
Running this scan on a regular basis and generating a diff report should help you detect new and suspicious devices on your home network.

Experienced Unix/Linux System Administrator with 20-year background in Systems Analysis, Problem Resolution and Engineering Application Support in a large distributed Unix and Windows server environment. Strong problem determination skills. Good knowledge of networking, remote diagnostic techniques, firewalls and network security. Extensive experience with engineering application and database servers, high-availability systems, high-performance computing clusters, and process automation.